cheqd & $CHEQ Explained
cheqd is the Payment & Trust Infrastructure for Credentials & Verifiable AI. We enable the creation of eID, digital credential businesses, personalised AI, and trust ecosystems. We provide privacy-preserving payments for data to incentivise its release from data siloes to enable impossible combinations of data to unlock new user experiences and personalised AI.
cheqd leverages Self-Sovereign Identity (SSI), Decentralised Identifiers (DIDs) and Verifiable Credentials (VCs) technologies to enable organisations to create their own Trusted Data ecosystems.
The more credentials organisations issue and verify on cheqd across diverse use cases, the higher the transaction volume on cheqd’s network, directly driving consumption and burn of $CHEQ.
This guide will explore everything you need to know about cheqd, how it works, and how the $CHEQ token plays a vital role in this groundbreaking identity solution.
The team behind cheqd
cheqd was co-founded by Fraser Edwards and Ankur Banerjee after their extensive experience at Accenture, where they spent six to seven years exploring various technologies, including biometrics, AI, blockchain, and network infrastructure. During their final years at Accenture, the focus shifted towards central bank digital currencies, cross-blockchain payments, and self-sovereign identity. It was in this period that Fraser and Ankur recognised a significant gap in the SSI space: while the concept of individuals owning their own data was widely appreciated, there was no clear pathway to monetisation. After repeatedly encountering this challenge in sales and business development meetings, the two co-founders decided to tackle the issue head-on. This decision led to the creation of cheqd in 2021. Their goal was to develop a sustainable business model that could unlock the true potential of self-sovereign identity. Javed Khattak later joined cheqd as a co-founder and CFO, bringing a wealth of financial and technical expertise. His background includes leading multi-billion-dollar funds and advising governments, central banks, and global brands.
Fraser: Follow him on Twitter | Connect on LinkedIn
Ankur: Follow him on Twitter | Connect on LinkedIn
Javed: Follow him on Twitter | Connect on LinkedIn
How cheqd Works
cheqd provides a vertical suite of solutions from cheqd Studio to Creds to establish trust and enable individuals and organisations to own, control and monetise their data in a portable privacy-preserving manner. The underlying privacy-preserving payment infrastructure Credential Payments creates a clear commercial model or revenue opportunity, allowing verifiers to directly pay issuers, verifiers to pay holders, or holders to pay issuers to unlock Credential Status information.
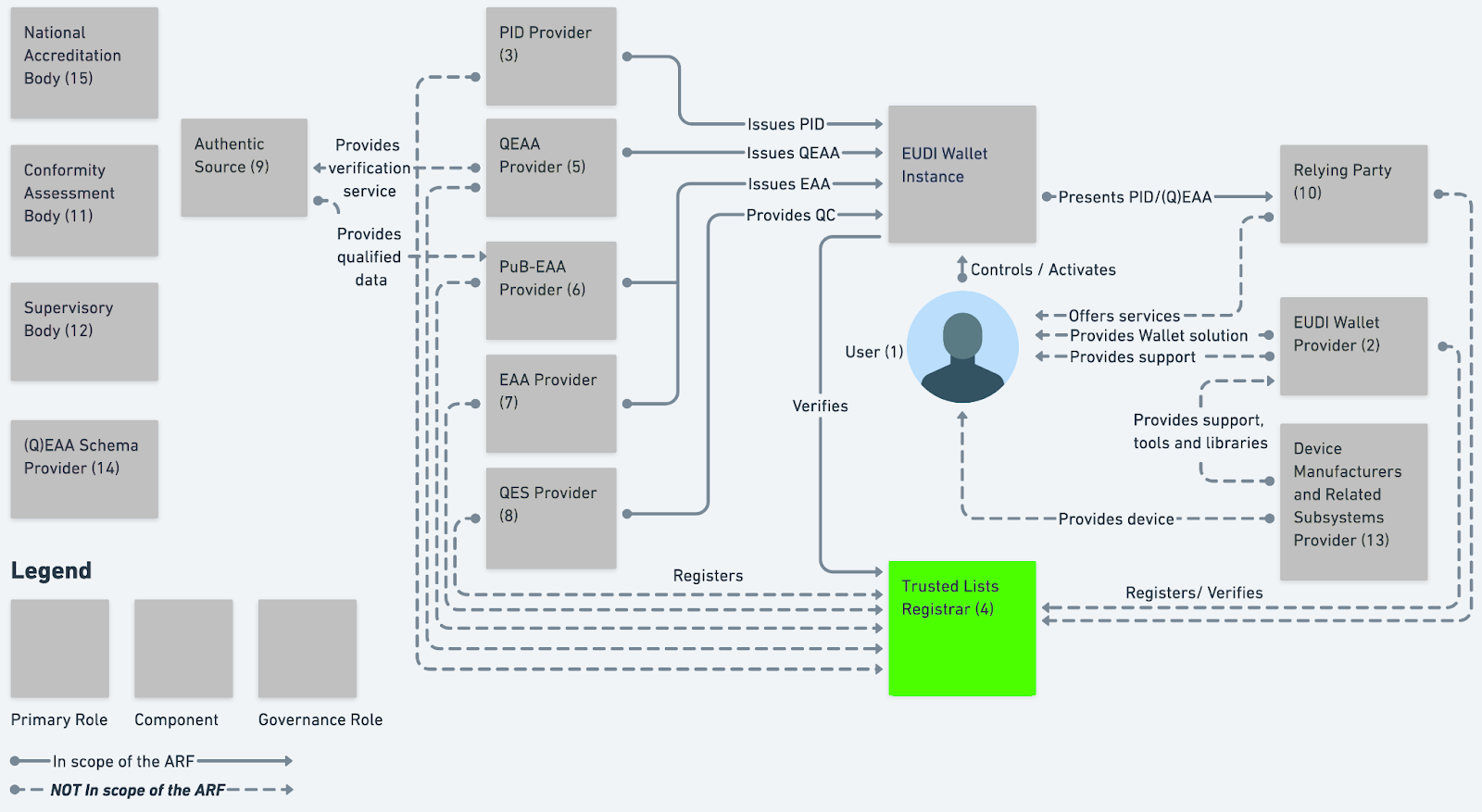
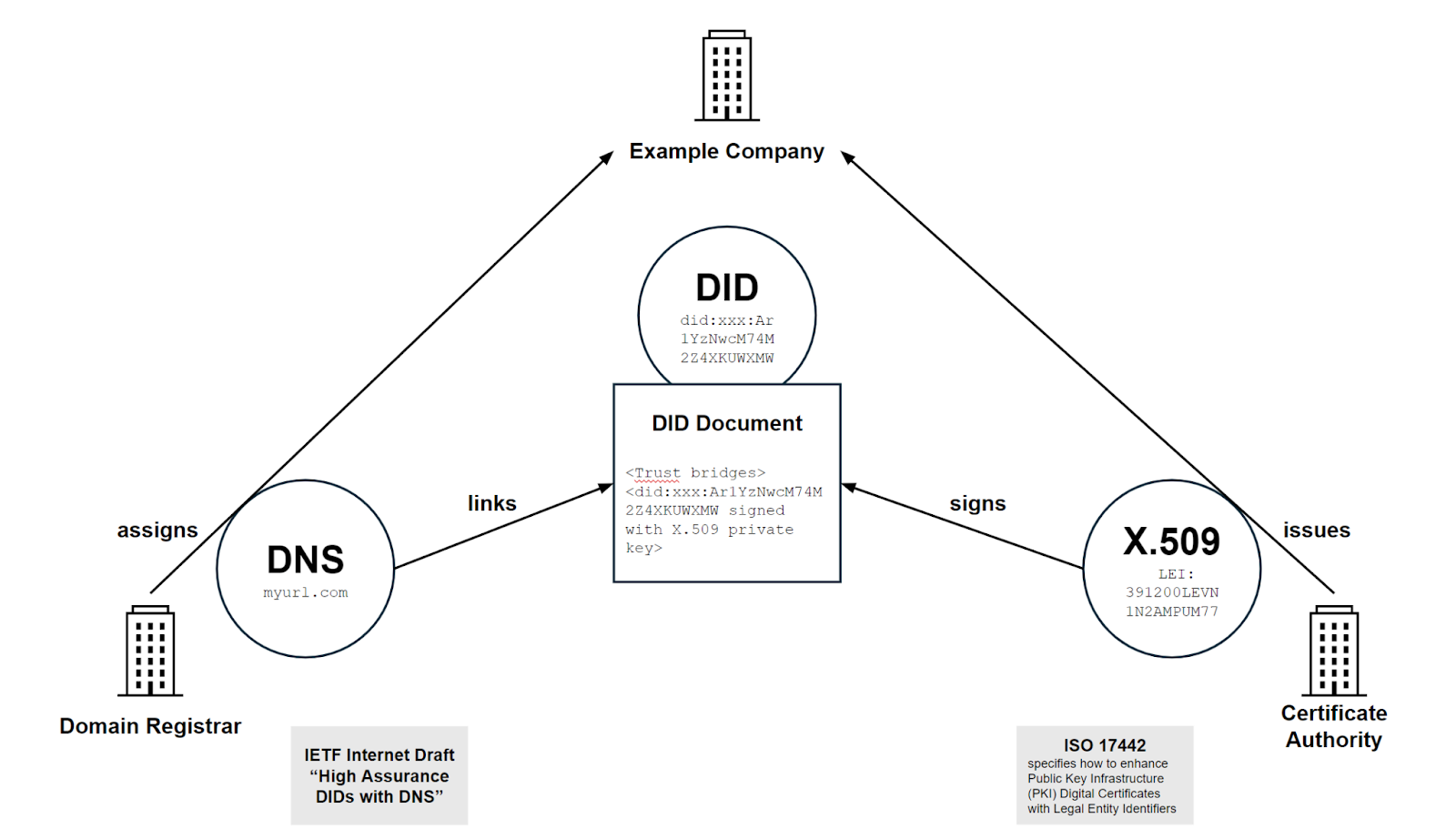
cheqd’s innovative approach is rooted in the use of Decentralised Identifiers (DIDs), Verifiable Credentials (VCs), Trust Registries, and technical standards developed by the World Wide Web Consortium (W3C).
Learn about the technicals

Use Case: Verifiable AI
The cheqd network and solution can be applied across diverse use cases ranging from reusable KYC to gaming, with the prominent one being verifiable AI. vAI leverages cheqd’s infrastructure to ensure trustworthiness in AI driven interactions.
- AI Agent: enable agents to carry verifiable credentials, which authenticate their identity, origin of training data, or legitimacy of outputs.
- Content Credentials: content credentials can be issued and verified, ensuring that authenticity claims are both trusted and easily accessible.
- Proof of Personhood: provide a decentralised framework for issuing and verifying credentials that prove an individual’s authenticity.
Contact us to build trust into your AI solution
More readings on Verifiable AI: The Agentic Economy Beyond Crypto | Our Verifiable AI Learnings | First vAI Partnership | Verifiable AI by cheqd | Use Cases of Verifiable AI Across Industries | Harnessing Verifiable AI to Defend Against Deepfakes | Verifiable AI in Action: Challenges and Opportunities | Origin of Verifiable AI:The Interplay of AI and Verifiable Credentials
What is the $CHEQ Token Used For?
The $CHEQ token is the backbone of the cheqd ecosystem, serving multiple purposes:
- Identity writes: Write Decentralised Identifiers (DIDs) and DID-Linked Resources to the network. Leads to a percentage of tokens burnt from the network.
- Credential Payments: Payments for decrypting on-ledger resources for the purpose of a Verifier paying a Credential Issuer.
- Governance: cheqd is a Delegated Proof of Stake network. $CHEQ holders have the power to vote on proposals, giving them a direct say in the future development of cheqd.
- Staking: Users can stake $CHEQ tokens to support the network and earn rewards in return, providing an additional layer of security and engagement.
- Incentives for Validators: Validators, who are responsible for maintaining the integrity of the network, are rewarded in $CHEQ for their work. This ensures that the network remains secure and operational.
cheqd is enhancing its tokenomics for $CHEQ holders with a deflationary mechanism and updated identity transaction pricing. Moving beyond gas-based fees, the new structure aligns fees with the network’s value, following models like Osmosis and Kujira. A portion of fees from identity transactions will reward validators and delegators, while another portion will be burned, reducing token supply.
This burn mechanism offsets staking rewards’ inflationary effects, aiming to stabilise the $CHEQ supply at one billion tokens. As network adoption grows, both rewards and token burns will increase, potentially boosting annual percentage yields (APY) and supporting the token’s value.
How to Own $CHEQ?
cheqd ($CHEQ) can be bought on popular cryptocurrency exchanges like Gate, BitMart, MEXC, MyContainer, and LBank (updated at the time of writing).
Experienced cryptocurrency users can opt to buy cheqd tokens via decentralised exchanges (DEXs) like Uniswap, Osmosis, Kujira, and Manta. Please check out their respective purchase guide as wrapped tokens might be involved in the process.
What is a cheqd Mainnet Wallet?
The CHEQ token can be purchased and transferred directly to a cheqd mainnet wallet address. There are two options for setting up a wallet and adding cheqd’s mainnet and testnet.
How to Stake $CHEQ?
Once you have set up your wallet, you have two options for staking: via OmniFlix or Leap Wallet.
For OmniFlix, head over to the cheqd staking and governance dashboard. You can either click “Stake Tokens” or click the tab in the right hand corner called “Stake”.
cheqd staking and governance dashboard
With Leap Wallet, follow the instructions provided to stake directly from there.
What is the cheqd Explorer?
Big Dipper is the cheqd Explorer. It is an open-source block explorer and token management tool serving over 10 proof-of-stake blockchains.
Where to Cast Votes for cheqd Proposals?
Holders of the native cheqd token, $CHEQ, can vote for proposals either on:
OmniFlix: https://cheqd.omniflix.co/proposals
Commonwealth: https://forum.cheqd.io