Presenting a Hybrid Approach to Trusted List Infrastructure and Management
Introduction
In June 2024, the latest version 1.4 of the European Digital Identity Wallet Architecture and Reference Framework (EU ARF) was made available by the European Commission; and a month later in July 2024, the first set of Draft Implementing Acts were published, including one on the EU Trust Framework. In each version, we are getting closer to an end-to-end trust model for European Digital Identity.
However, there is one aspect of the EUDI model that has remained relatively ambiguous, and moreover, this aspect is arguably one of the most crucial components of the model in establishing full end-to-end trust — that being, the construction of Trust Registries and Trusted Lists.
As shown in green on the diagram below, the “Trusted Lists Registrar” component of the EUDI model is a central point of trust, on top of which, all participants and entities in the EUDI ecosystem rely upon.
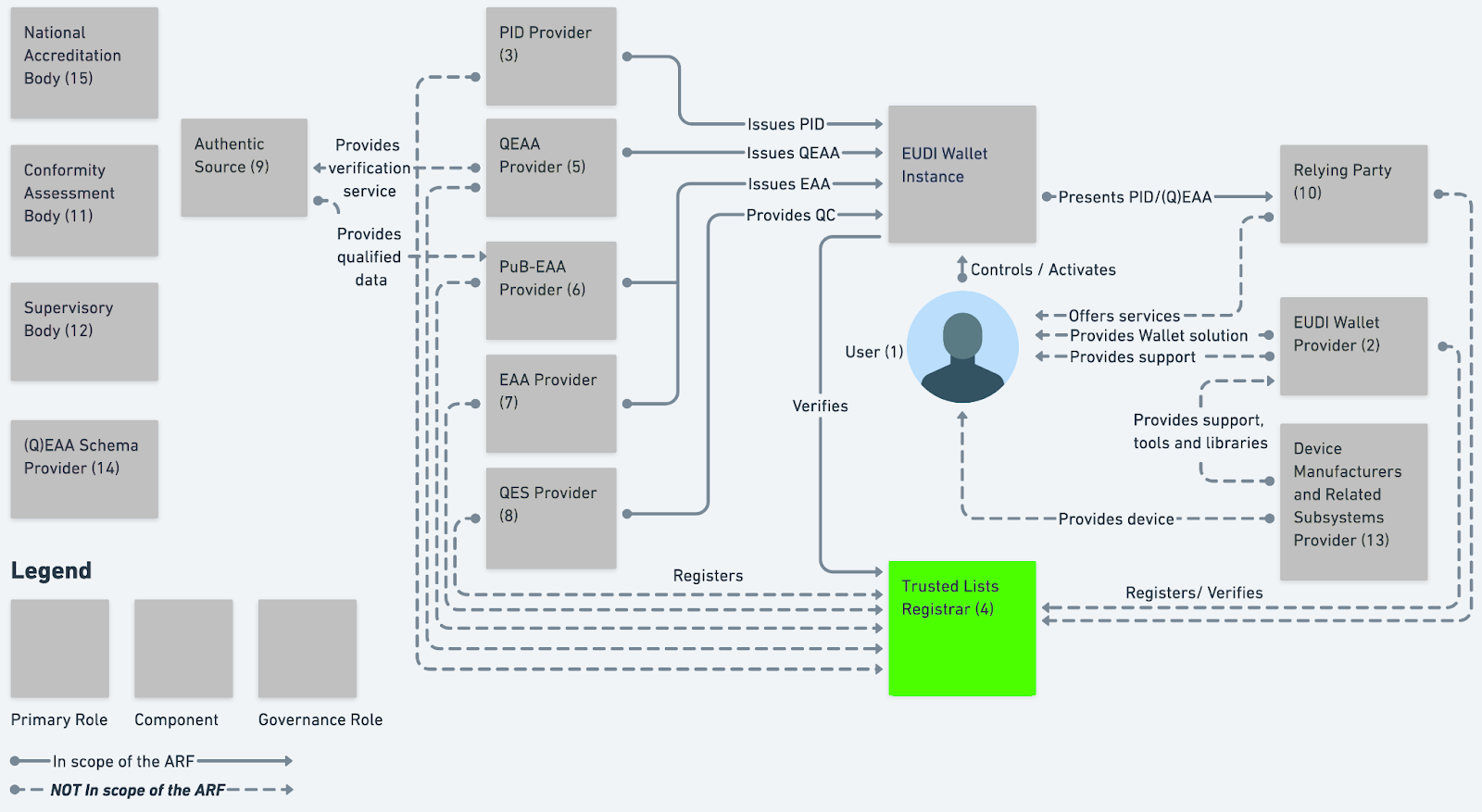
Trusted Lists are therefore pivotal in enabling relying parties to fully trust a credential presented to them. When consuming a digital credential, a relying party needs to verify not only the veracity of the issuer of that credential, but also the integrity and provenance of the “accreditation” and “authorisation” that issuer has to issue credentials within a particular governance framework. Secondly, the holder should be able to verify the integrity of the wallet provider or wallet agent; and finally, the holder should be able to verify the legitimacy of the relying party “verifier” application requesting digital credentials.
To explore this theme in more detail, this blog will centre around four core questions:
- What constitutes a trusted list?
- What is the problem with existing trusted lists?
- What is the difference between a “qualified” trust service and a “non-qualified” trust service?
- Why is there a significant opportunity in the market for a breakthrough trust registry model?
Through addressing these four questions, we will present an argument as to why cheqd is poised to position itself as a leader within the EUDI market and beyond, by solving an industry-wide problem regarding trusted list infrastructure.
Presenting a Hybrid Approach
There has been a longstanding debate regarding the applicability of DIDs to provide an equivalent function to X.509 certificates in digital credential ecosystems, owing to their ease of deployment, key management flexibility and inherent resolvability.
However, on their own, DIDs are not a complete solution because they need to be paired with a robust trust registry infrastructure to be an effective identifier model.
Together with the Fraunhofer Institute, we propose a hybrid approach to Trusted List and Trust Registry management, which blends the benefits of DID and DID-based trust models, with the “high” LoA trust infrastructure of DNS, traditional PKI and X.509 certificates.
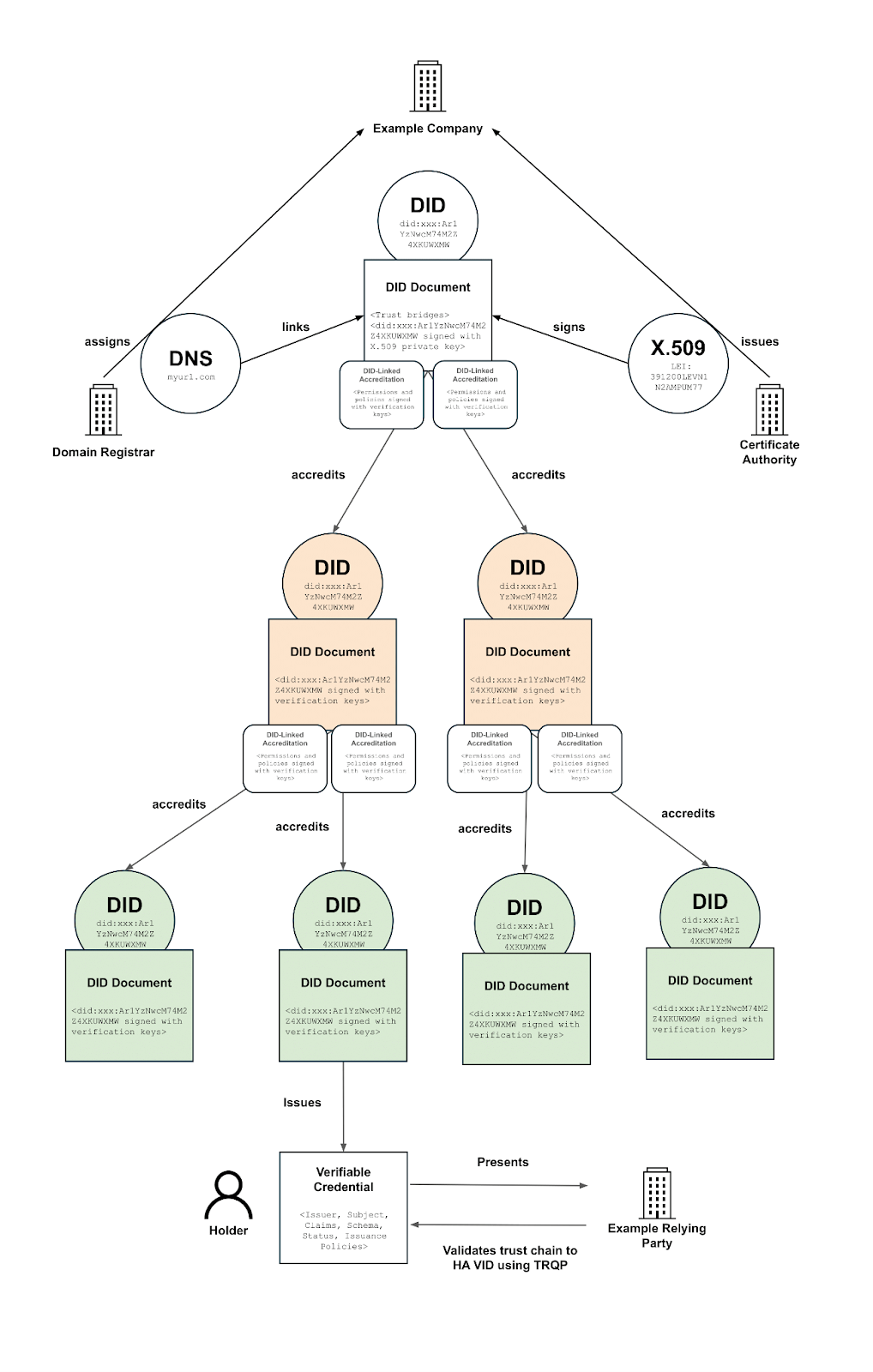
Throughout this blog, we will explain why a hybrid approach is necessary to improve on the existing traditional trust registry infrastructure, and how it creates a much more flexible and extensible architecture for digital credential ecosystems.
eIDAS 1.0 and traditional PKI
The concept of “Trusted Lists” within the EU ARF (and eIDAS 2.0) is an extension of the well-trodden path of trusted lists within eIDAS 1.0. Under the eIDAS framework, each of the 27 Member States maintains their own trusted list of “Qualified Trust Service Providers (QTSPs)” — namely, organisations that have been audited and approved to offer a set of “qualified” services, including:
- Qualified Electronic Signatures;
- Qualified Time Stamps; and
- Qualified Electronic Seals.
For digital document sharing, digital contracts and digital files shared between organisations, these “qualified” servicesestablish trust in the integrity of these actions through the use of Public Key Infrastructure (PKI) and secure digital certificates (generally type X.509). And through the eIDAS framework, the trust imbued in a QTSP in one Member State is given equivalent recognition across all Member States, creating an interoperable ecosystem of trust across the EU.
Furthermore, the eIDAS framework gives legal effect to electronic signatures backed by QTSPs, providing them the same level of trust as written signatures. This system has been fully functional for a number of years now, but there are a number of challenges that have inhibited mass adoption of eIDAS.
Challenges of eIDAS 1.0 and Traditional PKI
It is well documented that eIDAS 1.0 certificates have had lower levels of adoption than initially envisaged, which has accelerated the movement towards eIDAS 2.0. As such, it is important to reflect on the reasons why this occurred, before, as a community, we default to championing X.509 certificates as Roots of Trust for emerging digital credential ecosystems.
Many of the challenges faced under eIDAS 1.0 can be attributed to a lack of flexibility in how X.509 certificates can be used to convey trust between different member states, governance frameworks and certification schemes. This has led to a lack of interoperability between member states, whereby certificates issued in one member state are rarely able to be used in others.
X.509 certificates have undoubtedly been used for useful, robust and critical pieces of the web infrastructure stack. However, it is posited that they lack some of the fundamental capabilities to act as flexible, future-proofed roots of trust in a digital credential ecosystem, for three reasons:
- Square pegs in round holes: X.509 certificates were designed to answer the question “is this connection secure”, rather than “is this identifier trustworthy”. Therefore, each subsequent update to the X.509 spec (such as v3), has attempted to gradually create a more flexible and extensible data model. However, although X.509 v3 did include specific “extensions” to add more context on what a certificate was issued for and for what purpose, the scope of what you can achieve with an X.509 certificate is still relatively narrow.
- Difficulty in Handling Evolving Trust Relationships: In many domain-specific use cases, trust relationships are dynamic and require frequent updates based on changing conditions or regulatory requirements. X.509 certificates are static once issued, meaning they cannot be modified without reissuing a new certificate. This lack of adaptability is a significant drawback for domains that need to manage evolving trust relationships.
- Limited Support for Contextual and Granular Trust: X.509 certificates provide a binary level of trust (valid or not valid), lacking the ability to express more granular or contextual trust conditions. In contrast, many domain-specific applications might require credentials that can dynamically change trust levels based on context, permissions and policies depending on location, time, or user role.
It is important to highlight that this analysis is not a critique of X.509 certificates, in fact they have robustly stood the test of time to establish part of the backbone of the web today. What this is intended to question is whether X.509 certificates really are best placed for an efficient, flexible and scalable trust model for the EUDI ecosystem, where queries against trusted lists will be more vital and ubiquitous than ever before.
Extending Trusted Lists into the EU ARF
For the emerging EUDI ecosystem, “Trust Service Providers (TSPs)” will play a similar role in establishing “Roots of Trust” for digital credentials that are issued. In “decentralised identity” and “digital credential” ecosystems, credentials are cryptographically signed by an “issuer” and then are “issued” to a natural or legal person, who can then store the credential in their digital identity wallet. Therefore, these “issuers” need to be traced back to a trusted source.
For “Personal Identity (PID)” and “high” Level of Assurance credentials, they will be required to be traceable back to a “Qualified” TSP. The EUDI framework therefore establishes the concept of “Qualified Electronic Attestations of Attributes (QEAAs)” which are digital credentials that are cryptographically signed by a “QTSP”. The idea here is that a QEAAs have a higher level of trust assurance because a relying party can trace the credential back to a trusted X.509 certificate, backed by the eIDAS 1.0 framework.
Equally, the EUDI framework also acknowledges there will be non-qualified “Electronic Attestations of Attributes (EAAs)”. These will be more generic credentials of a “substantial” or “low” Level of Assurance. And rather than needing to be traceable back to a QTSP, these credentials may only need to be signed by a generic TSP. As such, there is much more flexibility in how EAAs may be implemented across different domain-specific use cases.
Importantly, for both EAAs and QEAAs, trust registries will play a very important role because relying parties will need to be able to make trust decisions about both these types of credentials, in a clear, accessible and interoperable way. And crucially, we need trust registry implementations that can delineate between different levels of assurance, permissions, policies and roles. If we are not cognizant of this requirement, there there is a real risk that the same challenges affecting the adoption of trusted certificates under eIDAS 1.0 will only get worse within the EUDI ecosystem.
For this reason, we have looked at alternative and hybrid approaches for trusted lists, trust registries and overall trust management which we see as an emerging opportunity in the EUDI market.
The Trust Registry Opportunity in EUDI
Over the past year of Large Scale Pilots and national projects such as DC4EU, the SPRIND Funke wallet prototype, there has been a narrow focus on High Level of Assurance (LoA) credentials, such as “Personal Identity (PID)” credentials.
Naturally, what has transpired from the focus on High LoA credentials is an equal focus on High LoA trust infrastructure and “Qualified Trust Service Providers”, namely using traditional PKI and X.509 certificate schemes. While these High LoA credentials are very important for the proper implementation of EUDI, in practice, they will only cover a minority of the total number of digital credential use cases.
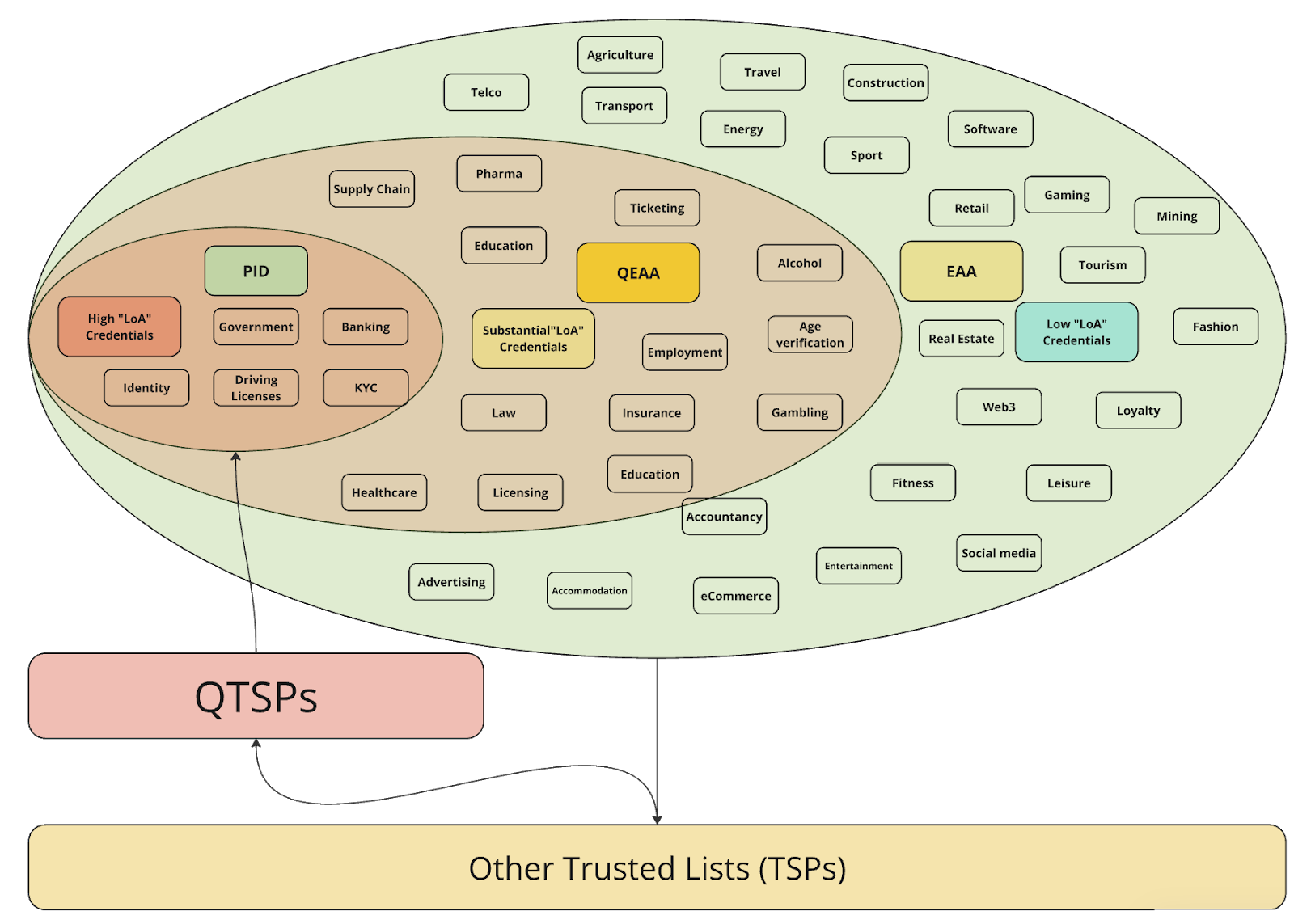
The diagram above shows how “PID” and “QEAA” credentials will cover less than half of the total number of industries expected to adopt Verifiable Credentials. As such, there is currently a gap in the EUDI market for providing trust registry infrastructure for Medium and Low LoA credentials that can emanate from “Non-Qualified Trust Service Providers” and coexist with the QEAA credentials.
Exploring the Hybrid Model
Together with the Fraunhofer Institute we have established an architecture that creates a far more extensible approach to trust registries for the emerging EUDI market. This approach combines three different approaches to trust registries into one overarching architecture:
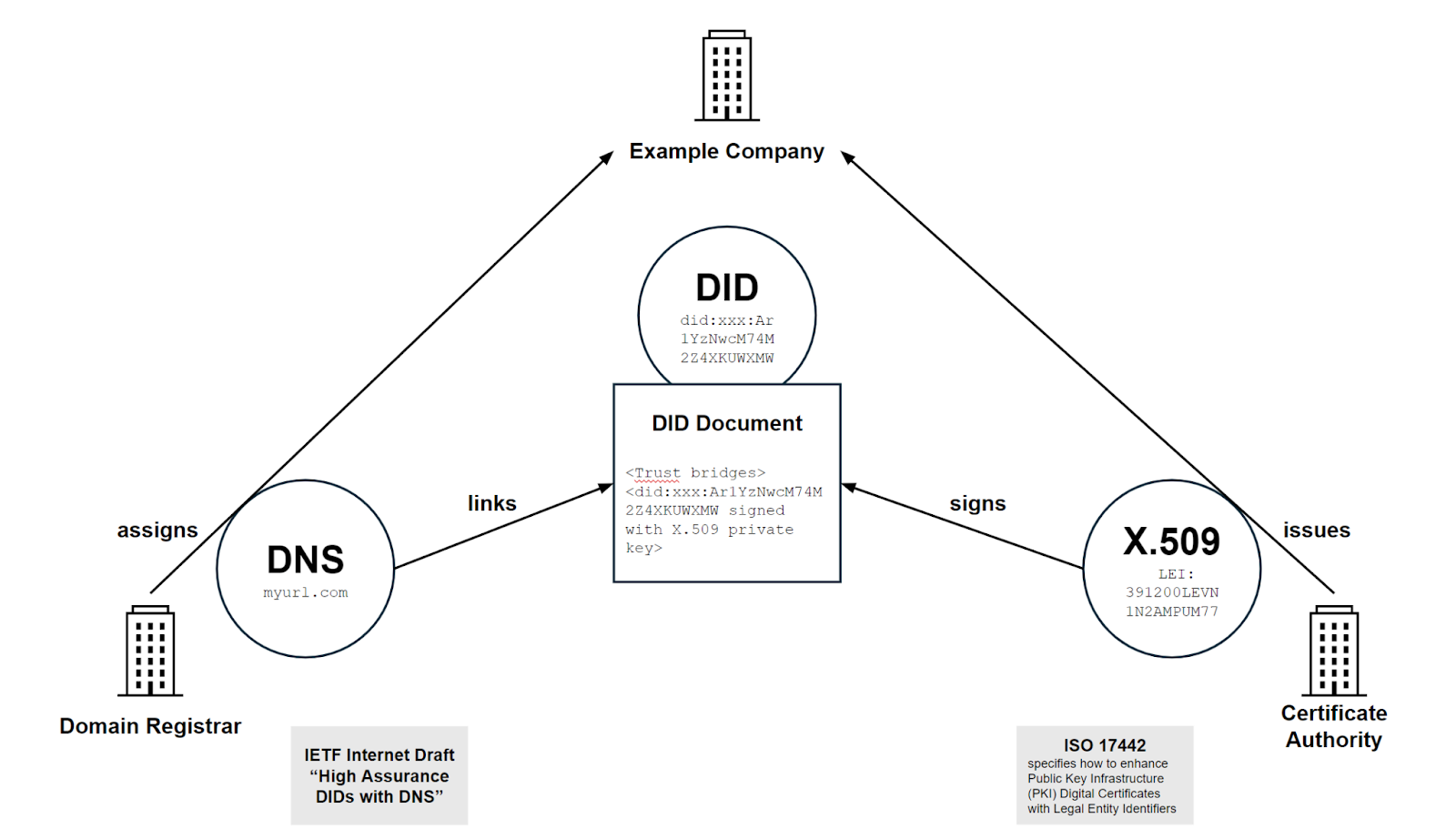
1. High Assurance Verifiable Identifiers
This model proposes that each governance framework establishes a set of High Assurance Verifiable Identifiers, building on top of the work of the Trust over IP High Assurance VID Task Force. This is an identifier that is cryptographically bridged to other equivalent identifiers for increased cryptographic assurance that the identifier belongs to a particular legal entity. For example, a “Root” DID can be stored within a DNS record, and can also be bridged with an X.509 certificate.
2. The European Blockchain Services Infrastructure (EBSI / Europeum) “Trust Chain” model
As part of this High Assurance VID, the Root organisation can “accredit” other organisations in its ecosystem, using issued “Verifiable Accreditations”. These Accreditations are Verifiable Credentials that are chained in a way whereby a relying party can traverse back to the High Assurance VID. Each Verifiable Accreditation can cryptographically prove that the TSP has been vetted and approved by a Root Authority. As a result, credentials issued by the TSP would inherit a level of trust derived from their association with the Root Authority, potentially enhancing their legal recognition and acceptance under eIDAS 2.0.
An organisation that issues an accreditation may also accredit other organisations with an array of permissions, including:
- Defining the schema of credentials or accreditations that the “subject” DID is permitted to issue;
- The jurisdictions under which the subject DID is permitted to operate within; and
- The lawful bases under which personal data within an issued verifiable credential must be handled, conforming with GDPR requirements by design.
This not only creates a “chain” of trust, but a chain of “governance” that is fully machine resolvable. Within the EBSI trust chain model, any “Credential” issued by an organisation can reference the URI for the “parent” accreditations up the trust chain, enabling a relying party to traverse the chain to the root of trust. This enables a far more flexible and domain-specific way of setting permissions and policies for each entity within the ecosystem, than relying on X.509 certs on their own.
3. W3C DID-Linked Resources for trust registry entries and standardised resolution
Within the proposed hybrid model, each “Verifiable Accreditation” is stored as a “DID-Linked Resource”, meaning that each Accreditation is uniquely resolvable, persistent and historically indexable. This allows issuers to include reference to trust registries and specific accreditations within issued credentials using a common DID URL syntax, as well as for verifier applications to resolve and traverse to each trust registry entry via the principles of DID URL resolution and dereferencing.
4. Alignment with OpenID Federation
OpenID Federation is an emerging specification that similarly creates hierarchical trust relationships for ecosystems. It shares many similarities to the proposed hybrid model in this blog, and there are ongoing efforts to expand the scope of OpenID Federation to allow a broader set of “Entity Identifiers” than simple web URLs.
Therefore, the medium-to-long term goal of the hybrid model is for it to become an implementation profile of a broader OpenID Federation model.
Benefits of the Hybrid Model
A hybrid model that combines X.509 certificates, DNS, Decentralised Identifiers (DIDs), and Verifiable Accreditations (stored as DID-Linked Resources) offers a range of benefits, blending the strengths of both traditional Public Key Infrastructure (PKI) and decentralised trust frameworks, including:
1. Enhanced Flexibility and Customisation:
The hybrid model allows for tailored trust solutions that can accommodate varying assurance levels across different domains. While X.509 certificates provide a high level of assurance for traditional applications (e.g., website authentication and secure communications), DIDs and Verifiable Accreditations offer more flexible, domain-specific credentials that can be customised to specific needs and contexts using customisable “permissions” and “policies” within each Verifiable Accreditation.
2. Scalability and Efficiency:
Decentralised elements like DIDs and Verifiable Accreditations reduce the dependency on centralised Certificate Authorities (CAs) and streamline the issuance, management, and revocation of trusted certificates. By only requiring X.509 certs for the Root of Trust, ecosystems can develop with lower operational overhead and faster scalability, which is crucial for the acceleration of EUDI ecosystems over the coming years.
3. Improved Interoperability:
Combining X.509 certificates with DNS, DIDs and Verifiable Accreditations enhances interoperability between legacy systems and emerging decentralised frameworks. This ensures a smoother transition for organisations adopting new identity standards without fully abandoning their existing PKI infrastructure, enabling a more seamless integration across diverse digital identity ecosystems.
4. Stronger Security and Redundancy:
The hybrid approach offers multiple layers of security, given X.509 certs, DNS and DIDs will be stored on different fundamental infrastructure. For example, using blockchain-based DIDs creates a dual-layered model that enhances resilience against attacks or failures, as the compromise of one trust layer does not necessarily affect the other. It provides redundancy and allows for a more robust security profile.
5. Horizontal, federated trust graphs:
Through implementing multiple federations of DIDs and Verifiable Accreditations (and iterating on top of the great work of OpenID Federation), the infrastructure is well placed for inter-ecosystem trust graphs, whereby different ecosystems can accredit each other to varying levels of assurance — creating a graph-like structure of cross-domain trust. This level of inter-ecosystem trust is currently the biggest blocker for more traditional X.509 based certificate schemes, owing to the lack of context specific detail which can be added — yet, it is a crucial component for a functional, interoperable digital credential future.
Conclusion
The urgency for innovative Trusted List models in the EUDI market cannot be overstated. As the European Union moves towards more stringent digital identity regulations and the demand for secure, scalable, and user-friendly digital solutions grows, the opportunity to lead in this space is ripe for the taking. We believe that organisations such as cheqd and EBSI that embrace the hybrid approach now will be well-positioned to establish themselves as pioneers in the digital identity landscape, benefiting from first-mover advantages and influencing the standards and frameworks that will govern the future of digital trust.
By leveraging the scalability, cost-effectiveness, and decentralisation of DID-based models while retaining the legal assurance of qualified services, this approach caters to the diverse needs of modern digital transactions — from high-assurance regulatory environments to dynamic, domain-specific use cases.
This is not just an opportunity — it is a strategic imperative for those looking to stay ahead in a rapidly evolving market. We also acknowledge that a strong trust registry alternative is a priority for many jurisdictions adopting digital credentials, and as such, we will next be looking at formalising and standardising the approach for wider adoption.






