Co-authored by Sid Lamichhane, Alex Tweeddale, and Patrick Herbke
Note: This blog post is based on the research paper: “DIDChain: Advancing Supply Chain Data Management with Decentralized Identifiers and Blockchain” by Herbke et al., accepted to be published at the 18th IEEE International Conference on Service-Oriented System Engineering 2024. During the proceeding of the conference, Herbke et al. won the best paper award for their contribution with DIDChain. Please reference the paper instead of this blog post.
Introduction
There is an increasing societal demand for consumers to be able to properly trace and verify the components, ingredients, and processes used for their purchased products.
More than ever before, consumers have greater choice in the food, pharmaceutical supplies, clothes and products that they buy; and concurrently, consumers have become more conscious about their health, environmental footprint and working conditions in the supply chain industry. Consumers are now interested in verifying that all the ingredients of food they purchase are healthy, pesticide-free or in accordance with their diet and allergies. Equally, consumers want to ensure that they do not support unfair trade, child labor, or environmental damage with their purchase.
Yet, the solution for enabling consumers to trace and verify products is not simple. The supply chain industry has been built on legacy systems for managing product data, such as centralised data silos and manual data processing, which predate the more recent demands for more transparency, verifiability, and trust assurance.
As a result, this gap between a product’s verifiability and its underlying composition, combined with the increase in consumerism, has led to a growing distrust in various industries, specifically with food, fashion, and pharmaceutical products.
In principle, it should be possible to offer product owners the chance to trace back the supply chain steps their product and its components have undergone. However, in practice, this is challenging because it requires all companies involved in a product’s supply chain to collaborate to reveal information about a specific product to its owner. Therefore, it becomes a considerable endeavour, depending on the complexity of a product and its supply chain’s level of globalisation.
To address this problem, we introduce a framework based on the cheqd blockchain network. Our framework endeavours to solve the aforementioned problems by giving owners and consumers of products a way to verify the supply chain of their products in a trustworthy manner.
cheqd for Verifiable Supply Chains
cheqd is a distributed ledger technology (DLT) that allows the sequential and chronological ordering of data that is highly accessible, persistently stored, and intrinsically verifiable. Technically, cheqd supports Decentralised Identifiers (DIDs) that are written into its blockchain. did:cheqd is a DID method with diverse functionality, enabling us to create a tree-based data structure to store the entire supply chain of a product on-chain. As the cheqd Network is public and permissionless, all on-chain data is public, permanent, and immutable. This not only leads to the supply chain’s verifiability but also makes it tansparent and trustworthy.
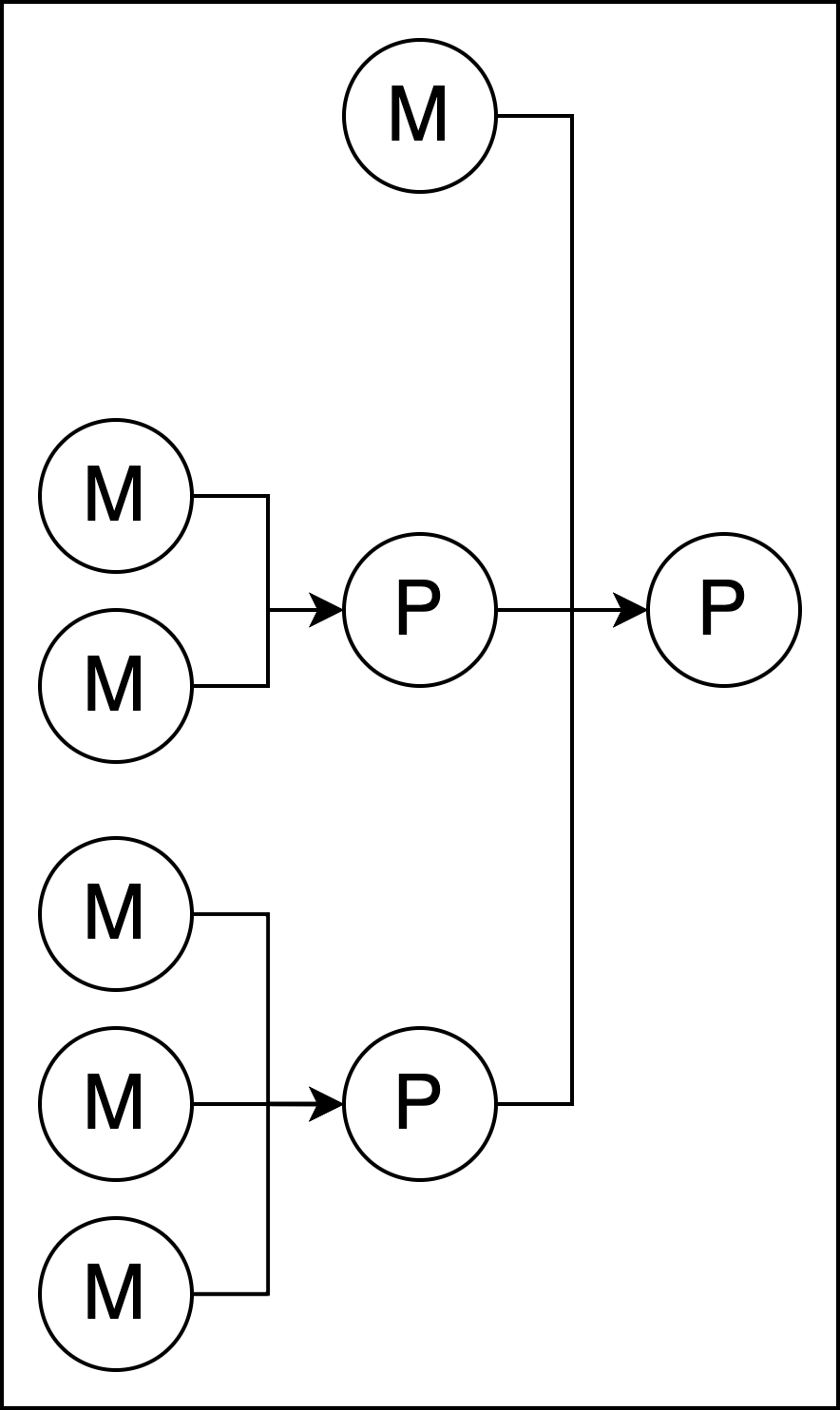
Figure 1 shows the tree-based data structure for modeling supply chains. Every node in the tree is a DID of type “cheqd” representing either a real-life product (P) or material (M). Products are defined to have components that can be either constituent products or materials. Materials such as oil, water, and copper are the tree leaves because they are produced, which does not require components like in the manufacturing of products. To store the relationships of the tree, the framework saves for each product the DID ID of all its components in the service section of its initial DID document.
However, having awareness of how other constituent products and materials assemble a product is not enough information for consumers to verify their lifecycle. Consumers also want to know what has happened to all the materials and constituent products used for their product. For this, our framework uses cheqd’s built-in on-chain DID document versioning management. Figure 2 shows how each DID document version corresponds to an event in the supply chain of the material or constituent product represented by the respective DID. It also shows how the built-in versioning management tracks the events in each DID document version’s metadata. This ultimately links all events together and gives them a timestamp, enabling a clear and holistic insight into a product’s supply chain.
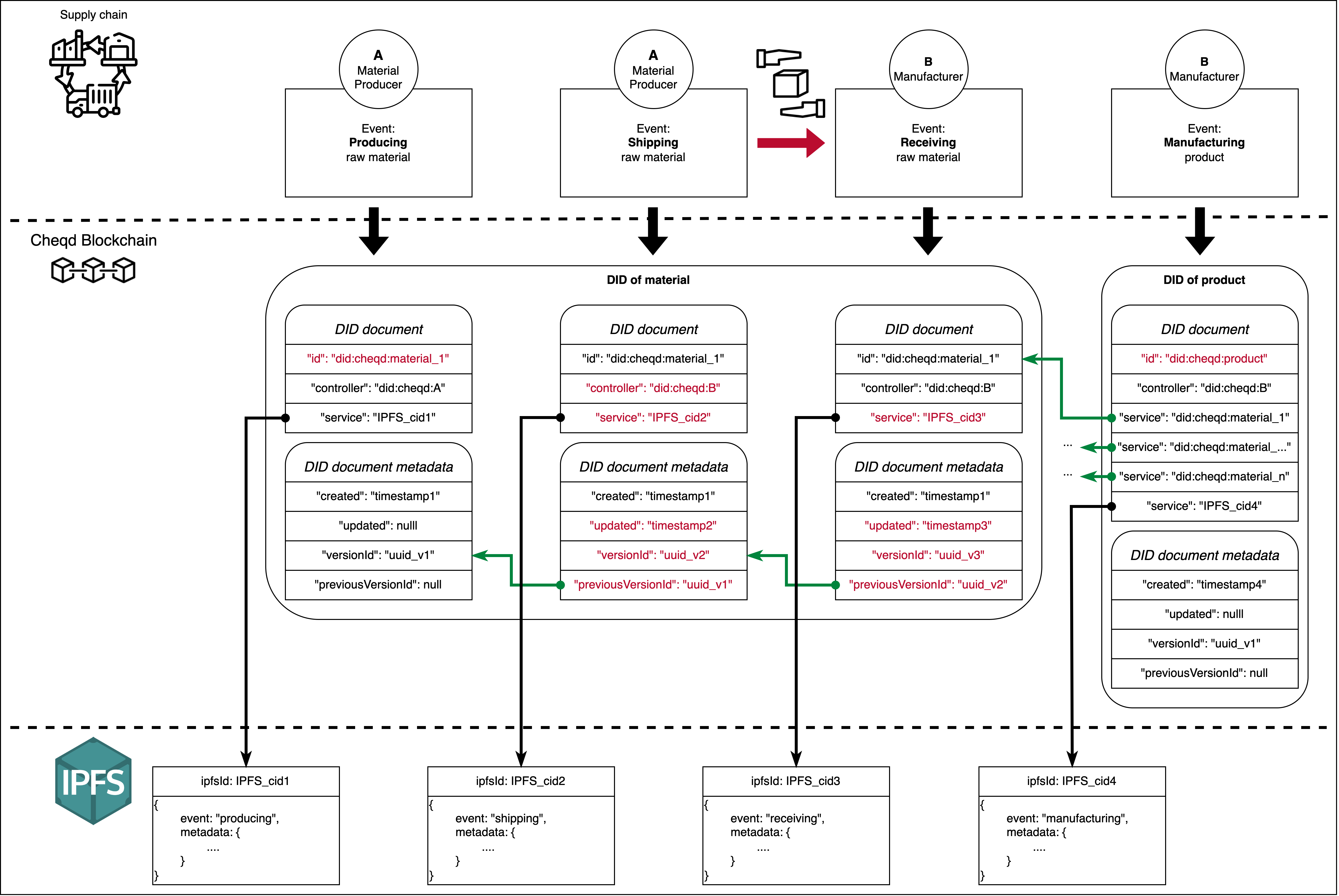
Our framework defines four atomic supply chain events: producing, shipping, receiving, and manufacturing. In the event of producing, a material is newly produced and registered as a DID. Shipping and receiving events both trigger an update to the DID document of the respective constituent product or material, automatically creating a new DID document version with a timestamp and a link to the previous version. When constituent products and materials are eventually sold, the shipping event takes place. It corresponds with a DID controller change in the new DID document version to reflect the change in ownership in real life. During manufacturing, a product is registered as a DID and its first document version contains a list of all DID IDs referencing the materials and constituent products used for its manufacturing.
Besides these event-specific happenings, each event is further detailed in a file stored in IPFS, the path of which is written in the corresponding DID document version. This minimises on-chain data storage and allows for infinite data scalability without comprising the framework’s data properties: public, permanent, and immutable. Alternatively, we can use cheqd’s DID-Linked Resources to keep all data on the cheqd Network. This alternative comes with the significant advantage of enabling the linked files to be secured with the same cryptographic integrity as the DID itself, as well as being flexible regarding the privacy level of the data.
Conclusion
As a result, our framework enables supply chain entities such as producers, manufacturers, and suppliers to make their actions transparent and traceable. Due to its rich functionalities, cheqd’s DID method simplifies the implementation of our framework. With its built-in on-chain versioning management, cheqd provides the crucial trust layer for our verifiable supply chain data management system framework, which is not possible with centralised or traditional infrastructure. Through this model, cheqd and other compatible DLT infrastructure can be a transformative use of technology for the supply chain industry, unlocking transparency, accountability, and trust.