A technical approach to building Trusted Data Markets, reducing the time-to-reliance and compliance costs in digital interactions.
Introduction
In our previous blog we discussed the thematic strands that underscore trust in markets, specifically data markets. We suggested that by introducing verifiable data into various interactions undertaken by market participants, we could add a new dynamic that reduced time-to-reliance whilst preserving self-selective disclosure of information.
Through introducing a new form of trust, we are able to invert the data paradigm of shadow markets — enabling new transactions, commercial models and use-cases to form. By altering these trust dynamics, cheqd provides infrastructure to support the advent of a new type of data economy, what we call: Trusted Data Markets.
This blog will look at how cheqd supports Trusted Data Markets from a technical perspective, and how components such as: Decentralized Identifiers (DIDs), Verifiable Credentials (VCs) and Trust Management Infrastructure (TMI) (such as Trust Registries (TRs) or Status Registries (SRs)) complement each other and provide different dynamics of a Trusted Data Market.
The “Trust Gap”
As discussed in “The Anatomy of a Trusted Data Market”, the composition of “trust” is a complex and interpersonal relationship between two parties. It is predicated on more than the mere reliance on a particular party; namely, it involves an “extra factor”, including the perception of good faith and the willingness to act in a credible way.
However, when considering “trust” in a digital context, it becomes increasingly challenging. As opposed to an “interpersonal” relationship, digital trust is often a “pseudonymous” relationship. Here we approach what is widely regarded by academics as the “trust gap”; the de facto lack of the capacity to make an informed judgement on the “extra factor” to build “trust” beyond “mere reliance”.
Therefore, to build a functional Trusted Data Market with cheqd, we need to augment the requirement for this “extra factor” using a combination of trust-building technologies and techniques.
See: Camila Mont'Alverne, Sumitra Badrinathan, Amy Ross Arguedas, Benjamin Toff, Richard Fletcher, and Rasmus Kleis Nielsen. The Trust Gap: How and Why News on Digital Platforms is viewed more Sceptically versus News in General. 2022. University of Oxford. Reuters Institute.
Available at: https://reutersinstitute.politics.ox.ac.uk/
The Technical Components of a Trusted Data Market
The crux of establishing a Trusted Data Market using cheqd centres around the interplay of three technical components, used to create digital trust:
- Decentralized Identifiers (DIDs)
- Verifiable Credentials (VCs)
- Trust Management Infrastructure (TMI) such as Trust Registries (TRs) or Status Registries (SRs).
When used together, these three components each tackle a different property of a Trusted Interaction, which will be discussed in turn:
- Legitimacy established by DIDs
- Integrity established by VCs
- Reputability established by TMI
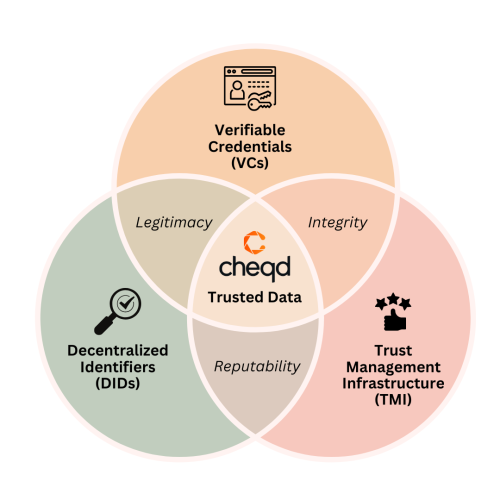
Legitimacy through Decentralized Identifiers
Decentralized Identifiers (DIDs) are a relatively new technical standard, ratified by the W3C as a formal recommendation in 2022, for uniquely identifying a particular entity in a digital domain. Each DID can be “resolved” to fetch a data file called a DID Document, which helps prove legitimacy in three ways:
Verification
DID Documents must contain signing keys, known as Verification Methods, which can be used to cryptographically sign other data files (such as Verifiable Credentials). If a DID and associated Verification Method is found referenced in another data file, that DID and it’s key can be challenged, and authenticated against, to prove that DID is in fact:
- Legitimate;
- Associated with a particular DID Document (discussed in point 2);
- Associated with any other DID-Linked Resource (discussed in point 3).
If a DID is proved to be legitimate, it is possible to infer that the data file signed by the DID has a higher level of trustworthiness.
Resolution
DID Documents may contain additional information about a particular entity (the DID Subject), through URI endpoints. Commonly, information about the DID Subject is written into the service section of a DID Document, which natively allows serviceEndpoints, pointing to other relevant information about the entity, such as perhaps their website, an email address or a social media profile.
This helps provide another layer of legitimacy for third parties who resolve a DID.
Resources
DID Documents may contain additional metadata about DID-Linked Resources (DLRs). DLRs are an extension to the DID Core spec, which may allow DIDs to be cryptographically associated with other digital resources, such as logos, documents or registries.
Using the same challenge and authentication mechanism, these associated DID-Linked Resources can be afforded a greater degree of legitimacy using the power of DIDs.
Importantly, DLRs can be used to create Trust Management Infrastructure (TMI) in a decentralized way, where Trust Registries (TRs) or Status Registries (SRs) may be made available and accessible using DID URLs.
The legitimacy provided by the DID authentication mechanism is the first ingredient needed to create a trusted digital relationship for a Trusted Data Market to function.
Integrity through Verifiable Credentials
Verifiable Credentials (VCs) are another type of data file, again formalised by the W3C as a standard, designed to ensure absolute integrity of the “claims” listed in the data file. A “claim” in this sense is an assertion about a particular entity; for example, this could be attesting to someone’s name, address, date of birth etc.
VCs are able to carry out this function because the “claims” contained in the credential are intrinsically verifiable through cryptographic “proofs”.
VCs dovetail well together with DIDs, since the “proof” embedded in the VC is able to be signed by DIDs and their associated Verification Method keys. This allows the VC “proof” to be challenged and authenticated against using the Public Key Infrastructure from the DID and associated DID Document.
Once the proof is embedded in the VC, the VC may also be serialised as a JSON Web Token (JWT) or use a Data Integrity proof (VC-DI), to create a representation of the Credential that is tamper-evident. This means that if any modification is made to the serialisation, the embedded “proof” will become unverifiable.
Commonly therefore, VCs are issued to a “holder”, who holds this in a data wallet, and these VCs are cryptographically signed by a DID of the issuing entity “issuer”. This enables the “holder” to prove to a third party that the Verifiable Credential has both:
- Legitimacy — since it is signed by a particular entities DID; and
- Integrity — since the cryptographic proof is tamper-evident.
Different cryptographic signature schemes can also be layered on top of VCs to provide additional benefits, such as:
- Selective disclosure: where only a selected subset of VC claims, or selected claims from multiple VCs, are presented in one tamper-evident format (e.g. SD-JWT).
- Zero-Knowledge Proofs (ZKPs): where a VC can use its legitimacy and integrity to prove a particular fact, in a yes/no challenge/response mechanism, without revealing the actual “claims” written into the VC (e.g. AnonCreds).
VCs are highly flexible in their design, with certain flavours being useful for specific use cases. However, each type maintains the same underlying focus on data integrity. This data integrity coupled with the legitimacy of DID authentication, is in many cases, enough for a verifier to build a level of “trust” in a digital interaction, reducing the time-to-reliance significantly.
Reputability through Trust Management Infrastructure
Trust Management Infrastructure (TMI) can be used to move the needle from “low/medium” trust digital interactions to “high” trust digital interactions. As such, this infrastructure may not always be required in a trusted data market — but may be relied upon when necessary.
DID-Linked Resources (DLRs) may be used to establish TMI in a decentralized way. Examples of common TMI for Trusted Data Markets are Trust Registries (TRs) which may ascertain whether a DID belongs to a trusted set; or Status Registries (SRs), which may be used to check if the VC status has been revoked or not. However, for the purposes of this paper, we will use TRs as the canonical TMI to explain the concept of reputability.
A TR is a data object where one entity publicly attests to the legitimacy of other entities. For example, a Health Regulator such as the Medicines and Healthcare products Regulatory Agency (MHRA) in the UK may create multiple trust registries of pharmaceutical manufacturers or wholesalers that are legally regulated to provide certain types of medicines, drugs or pharmaceutical products in the UK.
In the context of decentralised identity technology, TRs contain lists of DIDs pertaining to specific entities for a particular purpose. In the example above, MHRA could create a TR including the DIDs of each pharmaceutical manufacturer or wholesaler regulated to carry out a particular action.
Through resolving-to and parsing a TR, a verifier can traverse the DIDs and metadata that is listed to establish a root-of-trust and establish that the data they are receiving hits requisite levels of assurance for a specific governance framework.
TRs provides relying parties with additional assurance through this way of linking to a root-of-trust, resulting in:
- Reputability, since the “verifier” will be able to check that the “issuer” DID signing the “holder” VC is attested to by one or multiple other entities through a public TR; this layers on top of:
- Legitimacy (as previously discussed)
- Integrity (as previously discussed)
To conclude this section, the diagram below helps explain how the three technological components described in this section work in conjunction with one another — to build a comprehensive web of trust.
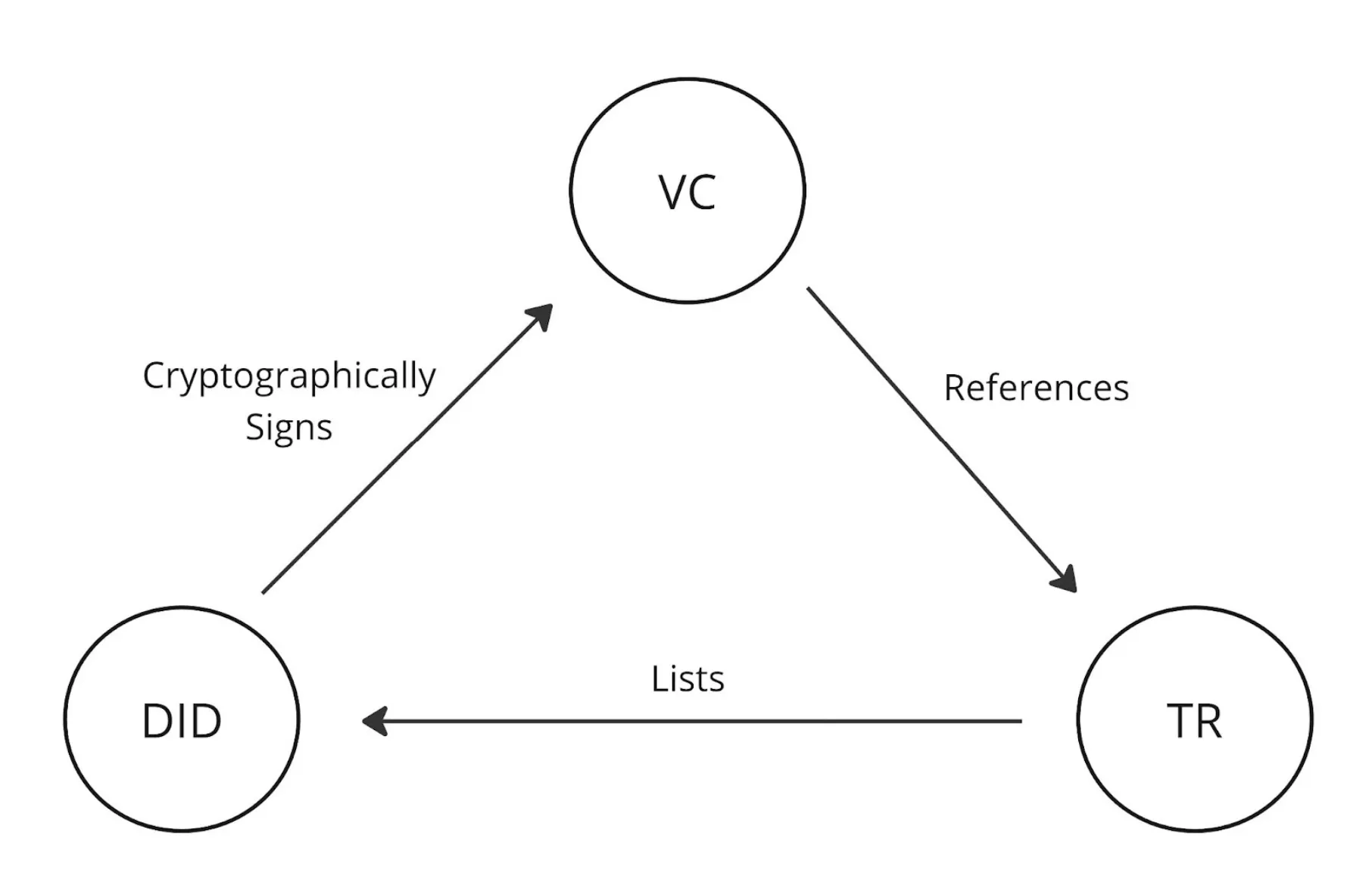
This diagram illustrates the following flows:
- A DID cryptographically signs a VC, which establishes Legitimacy and Integrity in the data the VC contains
- A VC references a TR (or other TMI), which establishes Legitimacy and Integrity that a TR is intended to be used by the verifier
- The TR provides additional information about the reputability of the DID, which establishes Legitimacy, Integrity and Reputability in the DID and signed VC which can be used to meet governance and compliance requirements.
Bridging the Trust Gap
The combination of DIDs, VCs and TMI goes a long way to move digital interactions beyond mere-reliance, since a “holder” (H) is able to prove that their claim is:
- Legitimate, since it is attested to by a particular “issuer” (I)
- Cryptographically untampered because the VC data model enables proof serialisation and data integrity
- Reputable, since one or multiple TRs can be referenced to where the issuer’s DID is attested to by third parties
For a relying party verifying the VC, “verifier” (V), this obfuscates the need to fully trust the “holder”, instead moving the burden of trust onto the strength of the technology and cryptography within the VC itself. This greatly closes the “Trust Gap” from necessitating a wide-berthed “interpersonal” human relationship, to a far narrower “inter-network” technical relationship.
Crucially, this combination of technologies also makes trust instantaneous. Since legitimacy, integrity and reputability can all be presented in one single proof. This significantly reduces the “Trust Gap” between mere-reliance and full trust. Thus, not only do these technologies create a new paradigm for digital trust, but they greatly increase the operational efficiency at which trust can be achieved — reducing the need for burdensome due-diligence checks and back-and-forths.
Using this type of instantaneous, inter-network trust, organisations can have have full confidence that:
- Other parties they are interacting with meet compliance requirements for their industry or use case, creating trusted markets;
- They themselves meet compliance requirements, as they can demonstrably assure third-party regulators that the data they receive from other parties has absolute legitimacy, integrity and sufficient reputability for a particular governance framework.
This type of inter-network and instantaneous digital trust, up until the advent of these technical components, has not been possible. Only now are we beginning to have the technical tooling to bridge the “Trust Gap”.
Making the Market
Up to this point we have largely discussed the technical components that constitute Trusted Data. This section will explain how cheqd supports the commercialisation of Trusted Data to build the fundamental concept here: Trusted Data Markets.
Core to cheqd’s objective of building Trusted Data Markets is the understanding that different digital interactions necessitate different levels of trust. Some interactions will be low-value interactions — such as using a VC attesting to a “name” and “DoB” to sign up for a gym membership. Others may be very high-value transactions — such as using a VC containing a “CCT General Practitioners’ Certificate” to onboard efficiently at a new hospital.
For this reason, the “Price of Trust” will vary depending on the determined value of the digital interaction, where low-value interactions may be free or low-cost; whereas, high-value interactions may be higher-cost.
To account for this differentiation, it was important when designing the infrastructure for Trusted Data Markets to ensure that the “verifier” has a choice in determining how much they want to spend on achieving “trust”. The outcome of associating a price with levels of trust is as follows:
- Legitimacy, via the authentication of a DID = Free
- Integrity, via the verification of a VC = Free
- Reputability, via the verification of a TR (or other TMI) = Paid
The logic here is that low-value interactions will generally not need to check a TR or verify reputability; yet, they should still be able to use the integrity and legitimacy benefits of DIDs and VCs at low-cost. A cost at this level would risk disincentivising the use of the technology because the potential financial loss from mere-reliance on a bad actor in low-value interactions would often be chosen over the price of trust.
Whereas, charging for reputability is a market that is already well established, for example existing KYC, KYB and general due-diligence checks are highly frequent in enterprise. Charging for the additional reputation of a Credential or DID will provide:
- A cost saving opportunity for entities to achieve a high-level of trust, compared to existing KYC and KYB mechanisms
- A time-efficiency bonus for achieving a high-level of trust, with trusted data being instantaneously verifiable — reducing the burden of regualtory compliance
- A never-before seen revenue opportunity for “issuers” of trusted data
Payment Gating Reputation
The way that cheqd supports the above objective is through payment gating the reputational arm of Trusted Data, Trust Management Infrastructure (TMI): Trust Registries (TR) or in an alternative use case, Status Registries (SR).
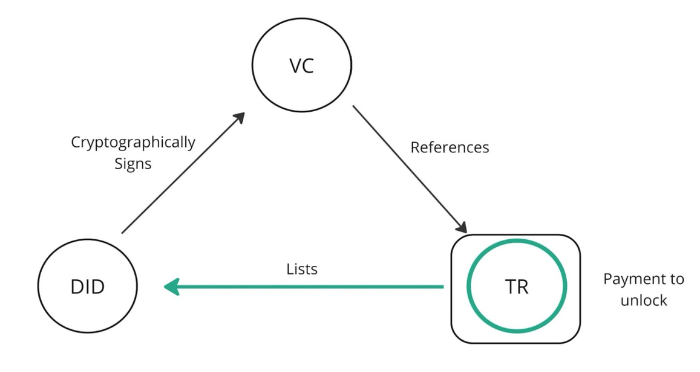
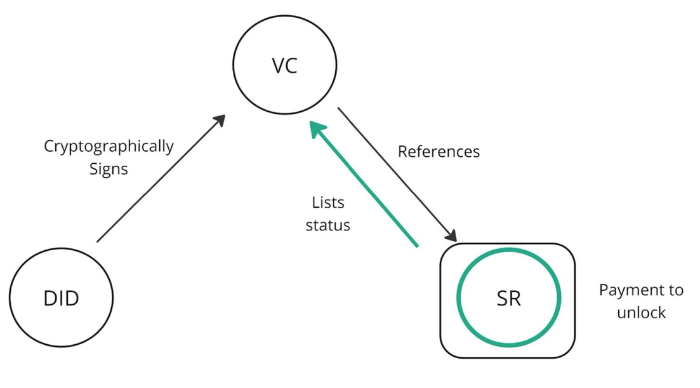
Using cheqd’s payment infrastructure, there are two market making operations at play here:
- “Issuers” (and in some cases “Regulators”) are able to set the market price of unlocking a TR or SR
- “Verifiers” are able to choose whether they want to pay to unlock the result of a TR or SR to achieve
- Payments will be made back to the “issuers” of the VC that is being presented to the “verifier”
Where it is hypothesised that:
- If a TR for a particular DID, or SR for a particular VC, has a high Level of Assurance (LoA), such as being created by a reputable entity, it is reasonably foreseeable that the price for that check may be higher than average.
- If the price of a TR or SR check is too high, the verifier will either: (a) Choose not to make the extra payment; or (b) Choose another TR to make the check against (if available)
- Once organisations and industries see the revenue opportunities from creating TRs, it is hypothesised that a competitive market will emerge — with a range of TRs with differing LoAs and associated range of prices.
This interplay of the use of DIDs, VCs and TMI, providing the composition of “Trusted Data” as one modality of market regulation; and, the economic cost of “instantaneous trust” vs the potential economic risk of “mere-reliance” as another modality, is ultimately what cheqd’s architecture facilitates as a “Trusted Data Market”.
The next blogs in this series will focus on the use-cases for Trusted Data Markets, and where we see markets requiring “instantaneous trust” for either: regulatory compliance, cost and time-saving, new revenue opportunities or a combination of all three.
We will explore how these use-cases present a clear product market fit for cheqd, cheqd’s partners and also the wider SSI ecosystem, projected to capture 550 billion dollars worth of value by 2030.






